
Welcome! Unlock Your First Offer Here

Welcome! Unlock Your First Offer Here

Welcome! Unlock Your First Offer Here
China's top anti-drone jammer manufacturer

When people talk about hijacking a drone, most think about hacking into its controller. But in my experience, the real vulnerability lies deeper—in the invisible signals that guide the drone through the sky. Spoofing those signals is one of the most subtle and powerful ways to redirect or disrupt a drone without ever touching its software.
Drone navigation spoofing works by imitating real GPS signals and feeding false data to the drone’s navigation system, causing it to miscalculate its location or follow a false route.

This attack doesn’t jam the drone. It doesn’t cut the signal. It simply tells the drone, “You’re somewhere else.” And most drones believe it. In this article, I’ll explain how spoofing works, how attackers generate these deceptive signals, what it takes to launch a spoofing attack—and how we can defend against it.
GPS spoofing isn’t science fiction—it’s a real method that tricks drones into flying the wrong way by feeding them fake location data. I’ve studied how these systems work and seen how quickly they can alter flight behavior.
Spoofing devices transmit false GPS signals with stronger power than real satellite signals. Drones lock onto these fake signals and calculate their position based on false data.

Drones typically use GPS signals from satellites to determine their position. These satellites send precise timing and position information from space. A drone receives signals from at least four satellites and calculates its position using triangulation. But the real signals are weak—typically around -130 dBm by the time they reach Earth.
Spoofing devices on the ground generate signals that mimic satellite messages but carry fake location and time data. Because these signals are closer, they reach the drone with more strength, causing the drone to “prefer” them.
The spoofed signals are carefully crafted to match the frequency (usually L1: 1575.42 MHz), modulation (BPSK), and pseudo-random code (C/A or P-code) of real GPS signals. When a drone locks onto the fake signal, it begins to navigate based on false coordinates, velocities, and timestamps—essentially steering off course without knowing it.
This doesn’t just cause a location error. It can cause the drone to crash, land in a trap zone, or endlessly hover in the wrong airspace—all while thinking everything is normal.
Spoofing isn’t just about sending false coordinates. It’s a game of timing, escalation, and subtle manipulation. I’ve seen how a skilled attacker can shift a drone’s behavior slowly and invisibly, guiding it step-by-step into the wrong place.
Spoofed signals gradually take control by first mimicking real satellite data, then injecting altered location and speed values to mislead the drone.
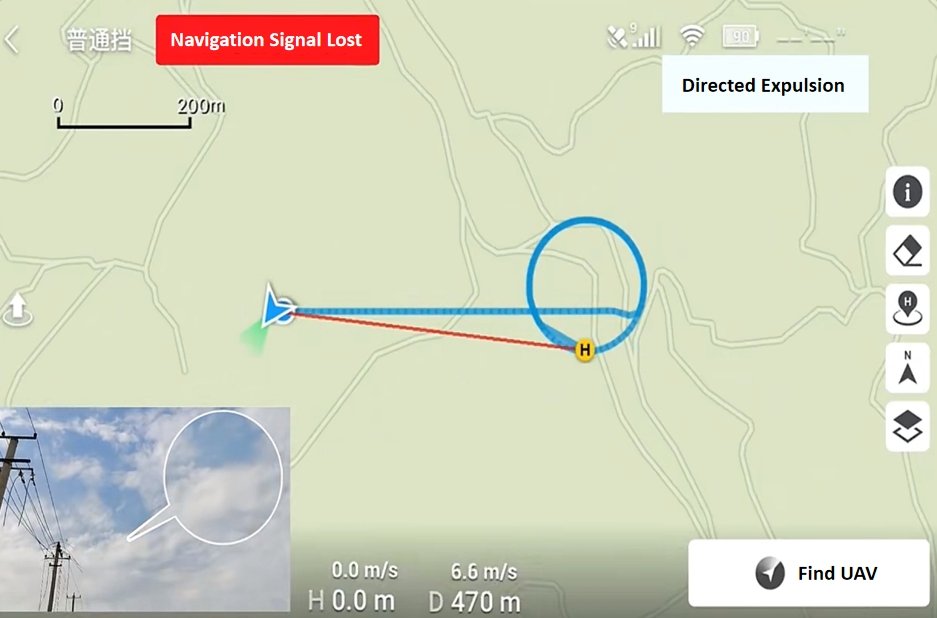
It starts with signal hijacking. The attacker’s device gradually increases the power of the spoofed signal until the drone’s receiver switches from real satellite data to the fake signal. This transition is subtle—often unnoticed by the drone’s internal diagnostics.
Once control is gained, the attacker modifies key navigation data:
If the goal is to redirect the drone, the attacker can slowly shift coordinates until the drone veers off course. If the goal is to land it, false coordinates can match the drone’s “safe landing” conditions and make it descend into a specific location.
What makes it dangerous is the realism. The drone receives all this input in the same format as real GPS data. There’s no red flag—unless extra safeguards are in place.
I’ve worked with electronic warfare engineers who showed me how spoofing devices are built. Some are sophisticated and military-grade. Others use off-the-shelf hardware. Either way, the concept is the same: generate believable fakes.
Spoofing attacks use signal generators, SDR (Software Defined Radio), GPS simulation software, and high-precision clocks to build and broadcast false satellite signals.

Spoofers work in different ways:
Creating realistic spoofing signals requires more than just equipment. It requires space-time synchronization. Devices must mimic satellite clock behavior (using rubidium or oven-controlled crystal clocks), simulate satellite orbits (based on Kepler’s laws), and match Doppler shifts caused by drone movement.
Advanced systems include:
In urban environments, attackers simulate multipath propagation by modeling signal reflections off buildings—making the fake signal more believable.
Defense starts with awareness. Too many drones still rely solely on GPS with no backup or cross-checks. I always recommend building in resilience—because even the best drone is vulnerable if it trusts the wrong signal.
Drones can defend against spoofing by using multi-signal navigation, signal consistency checks, encrypted GNSS, and fallback systems like inertial navigation.

From a technical point of view:
From a management perspective:
Ultimately, it’s about redundancy. No single solution can prevent spoofing completely—but combining detection with backup navigation gives drones a fighting chance.
Spoofing attacks don’t break drones—they mislead them. That’s what makes them dangerous. With the right equipment and knowledge, an attacker can take control without ever touching the drone. But as I’ve seen in real deployments, with smart design and layered defenses, drones can spot the lies. In a world where navigation is everything, signal trust is now part of drone survival.