
أهلاً وسهلاً بك! افتح عرضك الأول هنا

أهلاً وسهلاً بك! افتح عرضك الأول هنا

أهلاً وسهلاً بك! افتح عرضك الأول هنا
الشركة الصينية الرائدة في مجال تصنيع أجهزة التشويش المضادة للطائرات بدون طيار

تغير الطائرات بدون طيار كل شيء - من كيفية تصوير الأحداث إلى كيفية خوض الحروب. ولكن مع تزايد أعدادها، تزداد المخاطر أيضاً. لقد عملت في مجال تكنولوجيا الدفاع لفترة طويلة بما يكفي لرؤية هذا التحول يحدث في الوقت الفعلي. وسواء كان الأمر يتعلق بمظاهرة في وسط المدينة أو منطقة حظر جوي بالقرب من قاعدة عسكرية، فإن التحدي هو نفسه: كيف يمكننا إيقاف الطائرات بدون طيار المارقة بشكل آمن وسريع وقانوني؟

اثنان من أكثر الإجابات شيوعًا هما التشويش على إشارات الترددات اللاسلكية وانتحال نظام تحديد المواقع العالمي (GPS). لقد اختبرت كلاهما في مواقف حقيقية، من الملاعب المفتوحة إلى القواعد العسكرية الوهمية. في هذه المقالة, أريد أن أشرح لك كيف تعمل كل وسيلة، وأين هي الأنسب، وما هي نقاط قوتها وضعفها. إذا كنت مسؤولاً عن التخطيط الأمني أو الدفاعي، فأنت بحاجة إلى فهم هذه الأدوات - ليس فقط التقنية، بل المخاطر والتكاليف أيضاً.
تشويش التردد اللاسلكي هو طريقة القوة الغاشمة. إنه يغمر الهواء بالضوضاء عبر نفس الترددات التي تستخدمها الطائرات بدون طيار للتواصل-عادةً 2.4 جيجا هرتز أو 5.8 جيجا هرتز. عند القيام بذلك بشكل صحيح، تفقد الطائرة بدون طيار ارتباطها بوحدة التحكم، وإما أن تحوم أو تهبط أو تطير عائدة إلى المنزل.
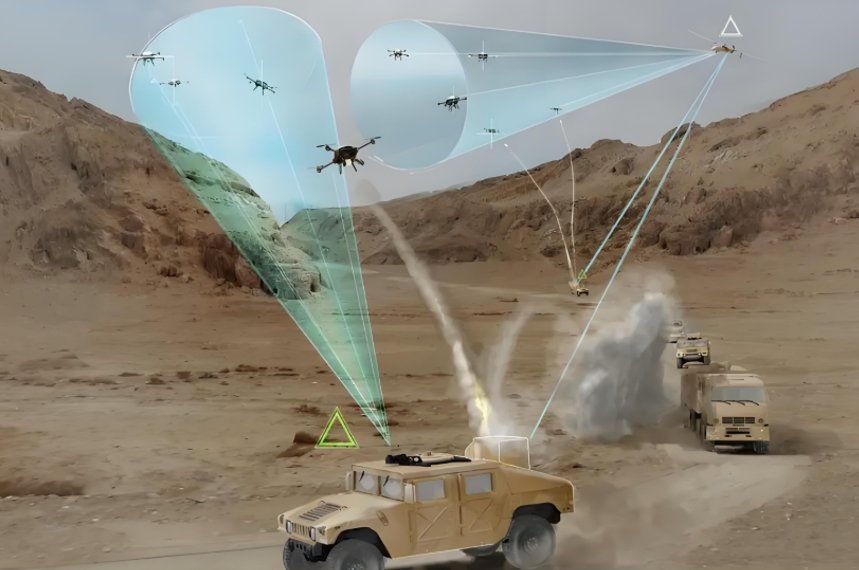
لقد استخدمت أجهزة تشويش محمولة باليد تعمل على الفور. في اللحظة التي نقوم فيها بتفعيلها، تتجمد الطائرات التجارية بدون طيار في الجو أو تتحطم في غضون ثوانٍ. ولكن هناك حدود. غالباً ما تقاوم الطائرات بدون طيار المزودة بتقنية التنقل بين الترددات أو الأوضاع المستقلة التشويش. بالإضافة إلى أن التشويش يؤثر على الأجهزة الأخرى القريبة منها - واي فاي وبلوتوث وحتى أجهزة الراديو في حالات الطوارئ. وهذا مصدر قلق قانوني وتقني كبير، خاصة في المدن.
| الميزة | التفاصيل |
|---|---|
| المبدأ | يفرط في تحميل نطاق الترددات اللاسلكية بالضوضاء |
| الأهداف الرئيسية | الطائرات بدون طيار الاستهلاكية المزودة بوصلات الترددات اللاسلكية |
| النطاق (نموذجي) | 1-2 كم في المناطق الحضرية، 3-5 كم في الحقول المفتوحة |
| سرعة الاستجابة | فوري |
| الآثار الجانبية | يؤثر على الأنظمة اللاسلكية القريبة |
| النشر | وحدات بسيطة محمولة باليد أو مثبتة |
| التكلفة | متوسطة (مئات إلى آلاف الدولارات) |
كيف يؤدي انتحال نظام تحديد المواقع العالمي (GPS) إلى تضليل الطائرات بدون طيار؟
انتحال نظام تحديد المواقع العالمي (GPS) أكثر هدوءاً. فبدلاً من قطع الطريق على الطائرة بدون طيار، فإنه يخدعها. يرسل المهاجم إشارات GPS مزيفة التي تتغلب على إشارات القمر الصناعي الحقيقية. "تعتقد" الطائرة بدون طيار أنها في مكان آخر، لذا فهي تتبع المسار الخاطئ أو تهبط في المكان الذي تريده.
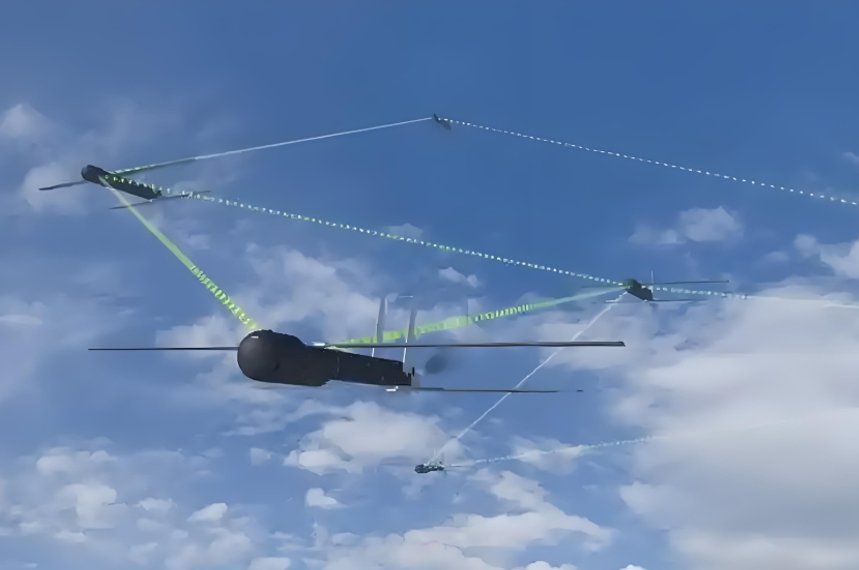
هذه الطريقة دقيقة ولكن يصعب تنفيذها. فهي تحتاج إلى أجهزة لاسلكية متخصصة محددة بالبرمجيات وتوقيت دقيق من أجل محاكاة إشارات الأقمار الصناعية. في أحد الاختبارات التي أجريناها، قمنا بخداع طائرة بدون طيار للتحليق بعيدًا عن منشأة آمنة والهبوط في "منطقة آمنة" على بعد 800 متر. لا تشويش ولا إنذارات - مجرد تضليل جراحي.
| الميزة | التفاصيل |
|---|---|
| المبدأ | يرسل إشارات GPS وهمية أقوى |
| الأهداف الرئيسية | الطائرات بدون طيار التي تعتمد على الملاحة بنظام GNSS |
| النطاق (نموذجي) | 2-3 كم، يمكن أن تمتد مع هوائيات عالية الكسب |
| سرعة الاستجابة | التأخير لبضع ثوان |
| الآثار الجانبية | قد يؤثر على نظام تحديد المواقع العالمي (GPS) في الهواتف والمركبات |
| النشر | معايرة ومزامنة معقدة-تحتاج إلى معايرة ومزامنة |
| التكلفة | مرتفع (عشرات الآلاف إلى الملايين) |
ما هي التقنية التي تناسب المواقف المختلفة؟
لقد عملت في مواقع كافية لأعرف أنه لا توجد إجابة شاملة. فكل موقع وحدث ومهمة تتطلب نهجاً مختلفاً. إليك كيف أقرر عادةً ما أستخدمه:

مقارنة نقاط القوة والقيود
| الميزة | تشويش إشارة الترددات اللاسلكية | انتحال نظام تحديد المواقع العالمي (GPS) |
|---|---|---|
| التحكم المباشر | نعم (قطع الأمر) | لا (إعادة توجيه مسار الرحلة) |
| الموثوقية | طائرات بدون طيار عالية مقابل طائرات بدون طيار بسيطة | طائرات بدون طيار عالية مقابل الطائرات بدون طيار المعتمدة على نظام تحديد المواقع العالمي (GPS) |
| القيود القانونية | عالية جداً | عالية للغاية |
| نصف قطر التصادم | واسع (تعطيل غير مقصود) | ضيق (منطقة الانتحال المركّز) |
| المقاومة المضادة | ضعيف ضد الطائرات بدون طيار ذاتية التشغيل | ضعيف ضد نظام تحديد المواقع العالمي المشفر |
ما التالي في مجال التكنولوجيا؟
أصبح التشويش على الترددات اللاسلكية أكثر دقة. نحن الآن نستخدم الذكاء الاصطناعي لتعلم إشارات الطائرة بدون طيار وتكييف التشويش أثناء الطيران. لقد رأيت هوائيات ذات مصفوفة مرحلية تتعقب طائرة بدون طيار وتشوش عليها بشكل اتجاهي، مثل ضوء كشاف من طاقة الترددات اللاسلكية.

أصبح انتحال النظام العالمي لتحديد المواقع متعدد الطبقات. يمكن لبعض الأنظمة تزييف نظام تحديد المواقع العالمي GPS وGLONASS وBiDou في آن واحد. في المختبرات، نقوم بتجربة "الانتحال التعاوني"، والذي يبدأ بالتشويش الناعم، ثم يخفف من حدة التشويش على الطائرة بدون طيار في منطقة نظام تحديد المواقع العالمي المزيف.
توزيع التكلفة
| فئة التكلفة | تشويش إشارة الترددات اللاسلكية | انتحال نظام تحديد المواقع العالمي (GPS) |
|---|---|---|
| المعدات | $500-$50,000 | $10،000-$1M+ |
| تكلفة التشغيل | معتدل (بطارية أو تيار متردد) | منخفضة (تعمل بالبطارية في الميدان) |
| الصيانة | متكررة (مكبرات الصوت، البلى) | نادر (الساعات الذرية تدوم طويلاً) |
| وقت النشر | < أقل من 10 دقائق | 30-60 دقيقة (معايرة الإشارة) |
الأفكار النهائية
لقد كنت على أسطح المنازل وفي المخابئ وخلف الشاشات باستخدام هاتين التقنيتين. ما تعلمته بسيط - استخدم الأداة التي تناسب الموقف. لا التشويش ولا الانتحال مثاليان. التشويش سريع ولكنه فوضوي. الانتحال نظيف ولكنه بطيء.
حسب خبرتي، فإن أفضل دفاع هو الدفاع متعدد الطبقات. أوصي بالبدء بالرادار والماسحات الضوئية للترددات اللاسلكية. استخدم الذكاء الاصطناعي لمعرفة نوع الطائرة بدون طيار التي تتعامل معها. ثم قم بالتشويش إذا كانت آمنة، والخداع إذا كانت متخفية. حتى أن بعض الأنظمة الجديدة تقوم بالتبديل بين الاثنين تلقائياً.

بغض النظر عما تختاره، اتبع القانون. هذه الأدوات قوية، ويمكن أن يؤثر سوء استخدامها على الأشخاص أو الأنظمة أو حتى الطائرات. لقد رأيت حالات حيث الإهمال أدى التشويش إلى تعطيل الشبكات القريبة. أنت لا تريد ذلك.
إذا كنت تخطط لنشر أنظمة مضادة للطائرات بدون طيار، فابدأ برسم خريطة لبيئتك. ما هي أنواع الطائرات بدون طيار الشائعة؟ ما مدى السرعة التي تحتاجها للرد؟ هل يوجد مدنيون بالقرب منك؟
تساعدك الإجابة على هذه الأسئلة في تحديد ليس فقط التكنولوجيا التي يجب استخدامها - ولكن كيفية استخدامها بمسؤولية.